Encourage Compliance
Travel Policy Optimization Tool
Detect and address deviations from your travel policy, safeguarding compliance and promoting your guidelines within your organization.
Always in the know
Uncover costly mistakes. Seize opportunites.
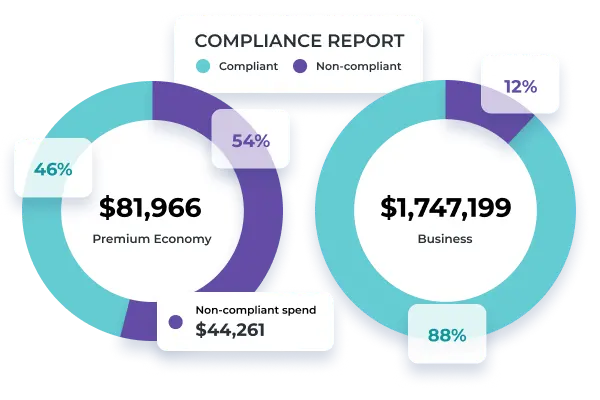
Tickets booked out of policy cost your business dearly. But how much exactly?
Stay informed and in control, and put a number on non-compliance costs with Oversee’s Policy Optimization reports.
Context-rich dashboards and reporting help you assess non-compliance.
Stay in control
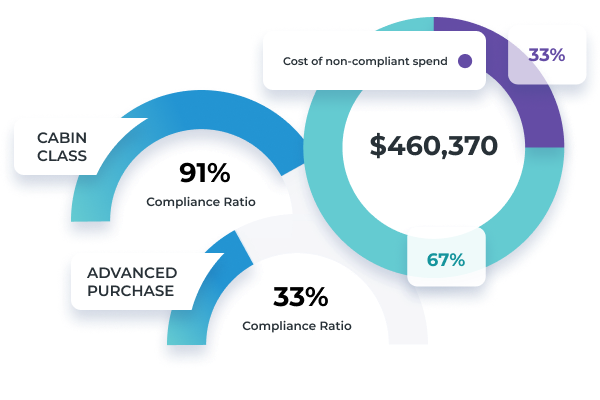
Cabin Class Compliance
With Oversee, monitoring cabin class policy compliance based on your criteria is easy. No guessing any further. Oversee calculates the costs associated with non-compliance for you.
- Break down non-compliant air spend by point-of-sale, cabin class, or haul type
- Know which flights were booked out of policy
Amend for Success
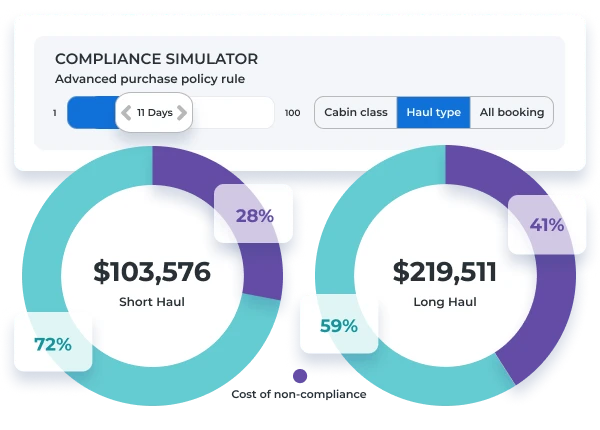
Advanced Purchase Compliance
Put your advance purchase policy to a reality check! Gain full visibility into current advanced purchase patterns and non-compliance costs.
- With our simulator, identify the optimal advance purchase window for your travelers and cost optimization
- Understand the severity of non-compliance on your corporate travel budget
- Program-wide or by point-of-sale, know the exact impact
LEARN MORE ABOUT OVERSEE’S POLICY OPTIMIZATION.
Get a personalized demo!
Our solutions experts are here to listen and share how your peers leverage Price Assurance and Program Optimization. Let us show you how we can support you, your company, and your travelers.













